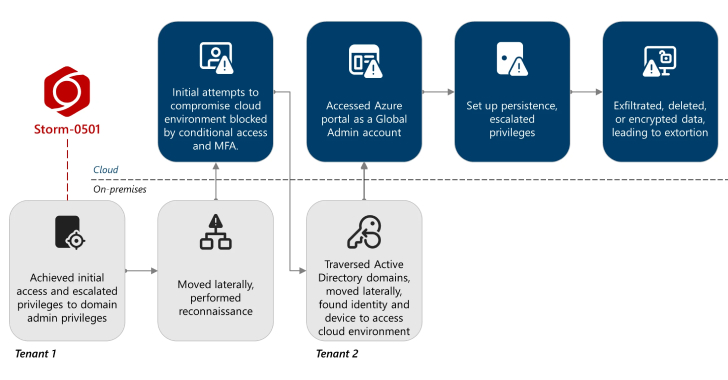
The financially motivated threat actor known as Storm-0501 has been observed refining its tactics to conduct data exfiltration and extortion attacks targeting cloud environments.
“Unlike traditional on-premises ransomware, where the threat actor typically deploys malware to encrypt critical files across endpoints within the compromised network and then negotiates for a decryption key, The financially motivated threat actor known as Storm-0501 has been observed refining its tactics to conduct data exfiltration and extortion attacks targeting cloud environments.
“Unlike traditional on-premises ransomware, where the threat actor typically deploys malware to encrypt critical files across endpoints within the compromised network and then negotiates for a decryption key,
- Anthropic AI Used to Automate Data Extortion Campaign darkreadingRob Wright
- ‘ZipLine’ Phishers Flip Script as Victims Email First darkreadingJai Vijayan, Contributing Writer
- Nevada’s State Agencies Shutter in Wake of Cyberattack darkreadingKristina Beek
- China Hijacks Captive Portals to Spy on Asian Diplomats darkreadingNate Nelson, Contributing Writer
- Google: Salesforce Attacks Stemmed From Third-Party App darkreadingElizabeth Montalbano, Contributing Writer
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)by Tech Jacks
- Tips and Tricks to Enhance Your Incident Response Proceduresby Tech Jacks
- Building a Security Roadmap for Your Company: Strategic Precision for Modern Enterprises by Tech Jacks
- The Power of Policy: How Creating Strong Standard Operating Procedures Expedites Security Initiativesby Tech Jacks
- Building a Future-Proof SOC: Strategies for CISOs and Infosec Leaders by Tech Jacks
- Security Gate Keeping – Annoying – Unhelpfulby Tech Jacks
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)


Leave A Reply