Cybersecurity researchers have uncovered a new malicious campaign that leverages a technique called Bring Your Own Vulnerable Driver (BYOVD) to disarm security protections and ultimately gain access to the infected system.
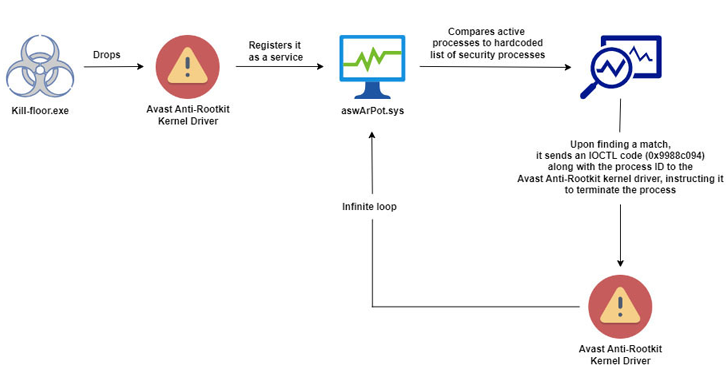
“This malware takes a more sinister route: it drops a legitimate Avast Anti-Rootkit driver (aswArPot.sys) and manipulates it to carry out its destructive agenda,” Trellix Cybersecurity researchers have uncovered a new malicious campaign that leverages a technique called Bring Your Own Vulnerable Driver (BYOVD) to disarm security protections and ultimately gain access to the infected system.
“This malware takes a more sinister route: it drops a legitimate Avast Anti-Rootkit driver (aswArPot.sys) and manipulates it to carry out its destructive agenda,” Trellix
- Wireshark 4.4.10 and 4.6.0 Released, (Sun, Oct 12th) SANS Internet Storm Center, InfoCON: green
- Experts Warn of Widespread SonicWall VPN Compromise Impacting Over 100 Accounts The Hacker [email protected] (The Hacker News)
- Hackers Turn Velociraptor DFIR Tool Into Weapon in LockBit Ransomware Attacks The Hacker [email protected] (The Hacker News)
- 1Password Addresses Critical AI Browser Agent Security Gap darkreadingArielle Waldman
- RondoDox Botnet: an ‘Exploit Shotgun’ for Edge Vulns darkreadingNate Nelson, Contributing Writer
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)by Tech Jacks
- Tips and Tricks to Enhance Your Incident Response Proceduresby Tech Jacks
- Building a Security Roadmap for Your Company: Strategic Precision for Modern Enterprises by Tech Jacks
- The Power of Policy: How Creating Strong Standard Operating Procedures Expedites Security Initiativesby Tech Jacks
- Building a Future-Proof SOC: Strategies for CISOs and Infosec Leaders by Tech Jacks
- Security Gate Keeping – Annoying – Unhelpfulby Tech Jacks
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)


Leave A Reply