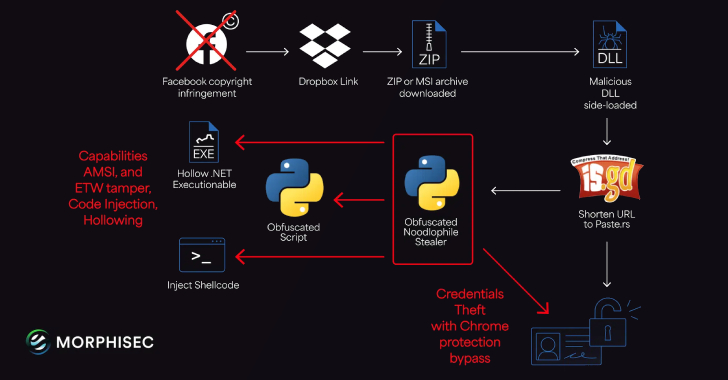
The threat actors behind the Noodlophile malware are leveraging spear-phishing emails and updated delivery mechanisms to deploy the information stealer in attacks aimed at enterprises located in the U.S., Europe, Baltic countries, and the Asia-Pacific (APAC) region.
“The Noodlophile campaign, active for over a year, now leverages advanced spear-phishing emails posing as copyright infringement The threat actors behind the Noodlophile malware are leveraging spear-phishing emails and updated delivery mechanisms to deploy the information stealer in attacks aimed at enterprises located in the U.S., Europe, Baltic countries, and the Asia-Pacific (APAC) region.
“The Noodlophile campaign, active for over a year, now leverages advanced spear-phishing emails posing as copyright infringement
- ‘K2 Think’ AI Model Jailbroken Mere Hours After Release darkreadingNate Nelson, Contributing Writer
- Russian APT Attacks Kazakhstan’s Largest Oil Company darkreadingNate Nelson, Contributing Writer
- SonicWall SSL VPN Flaw and Misconfigurations Actively Exploited by Akira Ransomware Hackers The Hacker [email protected] (The Hacker News)
- Fake Madgicx Plus and SocialMetrics Extensions Are Hijacking Meta Business Accounts The Hacker [email protected] (The Hacker News)
- Cracking the Boardroom Code: Helping CISOs Speak the Language of Business The Hacker [email protected] (The Hacker News)
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)by Tech Jacks
- Tips and Tricks to Enhance Your Incident Response Proceduresby Tech Jacks
- Building a Security Roadmap for Your Company: Strategic Precision for Modern Enterprises by Tech Jacks
- The Power of Policy: How Creating Strong Standard Operating Procedures Expedites Security Initiativesby Tech Jacks
- Building a Future-Proof SOC: Strategies for CISOs and Infosec Leaders by Tech Jacks
- Security Gate Keeping – Annoying – Unhelpfulby Tech Jacks
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)


Leave A Reply