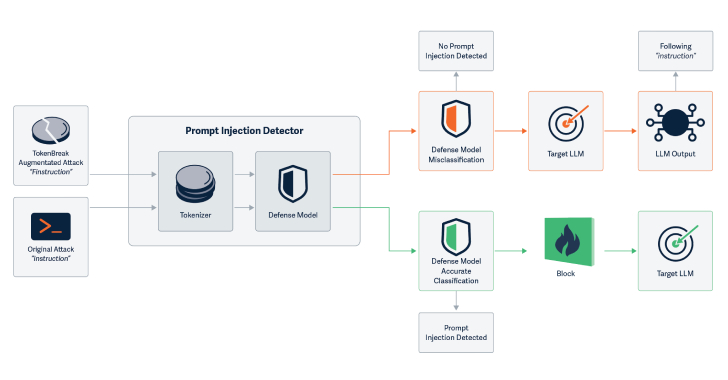
Cybersecurity researchers have discovered a novel attack technique called TokenBreak that can be used to bypass a large language model’s (LLM) safety and content moderation guardrails with just a single character change.
“The TokenBreak attack targets a text classification model’s tokenization strategy to induce false negatives, leaving end targets vulnerable to attacks that the implemented Cybersecurity researchers have discovered a novel attack technique called TokenBreak that can be used to bypass a large language model’s (LLM) safety and content moderation guardrails with just a single character change.
“The TokenBreak attack targets a text classification model’s tokenization strategy to induce false negatives, leaving end targets vulnerable to attacks that the implemented
- Over 269,000 Websites Infected with JSFireTruck JavaScript Malware in One Month The Hacker [email protected] (The Hacker News)
- Why CISOs Must Align Business Objectives & Cybersecurity darkreadingChad E. LeMaire
- Cyberattacks on Humanitarian Orgs Jump Worldwide darkreadingRobert Lemos, Contributing Writer
- Ransomware Gangs Exploit Unpatched SimpleHelp Flaws to Target Victims with Double Extortion The Hacker [email protected] (The Hacker News)
- CTEM is the New SOC: Shifting from Monitoring Alerts to Measuring Risk The Hacker [email protected] (The Hacker News)
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)by Tech Jacks
- Tips and Tricks to Enhance Your Incident Response Proceduresby Tech Jacks
- Building a Security Roadmap for Your Company: Strategic Precision for Modern Enterprises by Tech Jacks
- The Power of Policy: How Creating Strong Standard Operating Procedures Expedites Security Initiativesby Tech Jacks
- Building a Future-Proof SOC: Strategies for CISOs and Infosec Leaders by Tech Jacks
- Security Gate Keeping – Annoying – Unhelpfulby Tech Jacks
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)


Leave A Reply