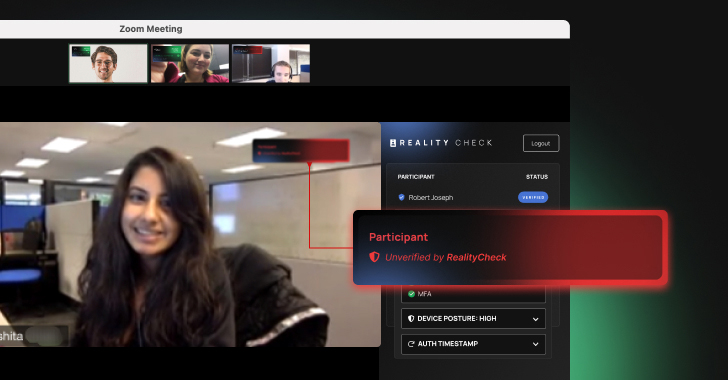
Artificial Intelligence (AI) has rapidly evolved from a futuristic concept to a potent weapon in the hands of bad actors. Today, AI-based attacks are not just theoretical threats—they’re happening across industries and outpacing traditional defense mechanisms.
The solution, however, is not futuristic. It turns out a properly designed identity security platform is able to deliver defenses Artificial Intelligence (AI) has rapidly evolved from a futuristic concept to a potent weapon in the hands of bad actors. Today, AI-based attacks are not just theoretical threats—they’re happening across industries and outpacing traditional defense mechanisms.
The solution, however, is not futuristic. It turns out a properly designed identity security platform is able to deliver defenses
- ISC Stormcast For Thursday, September 11th, 2025 https://isc.sans.edu/podcastdetail/9608, (Thu, Sep 11th) SANS Internet Storm Center, InfoCON: green
- DShield SIEM Docker Updates, (Wed, Sep 10th) SANS Internet Storm Center, InfoCON: green
- Students Pose Inside Threat to Education Sector darkreadingArielle Waldman
- Chinese Hackers Allegedly Pose as US Lawmaker darkreadingAlexander Culafi
- Chinese APT Deploys EggStreme Fileless Malware to Breach Philippine Military Systems The Hacker [email protected] (The Hacker News)
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)by Tech Jacks
- Tips and Tricks to Enhance Your Incident Response Proceduresby Tech Jacks
- Building a Security Roadmap for Your Company: Strategic Precision for Modern Enterprises by Tech Jacks
- The Power of Policy: How Creating Strong Standard Operating Procedures Expedites Security Initiativesby Tech Jacks
- Building a Future-Proof SOC: Strategies for CISOs and Infosec Leaders by Tech Jacks
- Security Gate Keeping – Annoying – Unhelpfulby Tech Jacks
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)


Leave A Reply