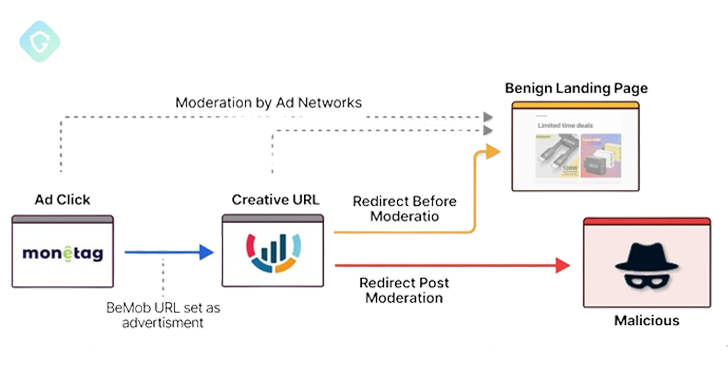
Cybersecurity researchers have shed light on a previously undocumented aspect associated with ClickFix-style attacks that hinge on taking advantage of a single ad network service as part of a malvertising-driven information stealer campaign dubbed DeceptionAds.
“Entirely reliant on a single ad network for propagation, this campaign showcases the core mechanisms of malvertising — delivering over Cybersecurity researchers have shed light on a previously undocumented aspect associated with ClickFix-style attacks that hinge on taking advantage of a single ad network service as part of a malvertising-driven information stealer campaign dubbed DeceptionAds.
“Entirely reliant on a single ad network for propagation, this campaign showcases the core mechanisms of malvertising — delivering over
- 1Password Addresses Critical AI Browser Agent Security Gap darkreadingArielle Waldman
- RondoDox Botnet: an ‘Exploit Shotgun’ for Edge Vulns darkreadingNate Nelson, Contributing Writer
- The Fight Against Ransomware Heats Up on the Factory Floor darkreadingArielle Waldman
- Feds Shutter ShinyHunters Salesforce Extortion Site darkreadingKristina Beek
- DDoS Botnet Aisuru Blankets US ISPs in Record DDoS Krebs on SecurityBrianKrebs
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)by Tech Jacks
- Tips and Tricks to Enhance Your Incident Response Proceduresby Tech Jacks
- Building a Security Roadmap for Your Company: Strategic Precision for Modern Enterprises by Tech Jacks
- The Power of Policy: How Creating Strong Standard Operating Procedures Expedites Security Initiativesby Tech Jacks
- Building a Future-Proof SOC: Strategies for CISOs and Infosec Leaders by Tech Jacks
- Security Gate Keeping – Annoying – Unhelpfulby Tech Jacks
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)


Leave A Reply