Cloud Security & Governance Primer

Characteristics of Cloud Computing
On-demand self-service. A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider.
Broad network access. Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations).
Resource pooling. The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. There is a sense of location independence in that the customer generally has no control or knowledge over the exact location of the provided resources but may be able to specify location at a higher level of abstraction (e.g., country, state, or datacenter). Examples of resources include storage, processing, memory, and network bandwidth.
Rapid elasticity. Capabilities can be elastically provisioned and released, in some cases automatically, to scale rapidly outward and inward commensurate with demand. To the consumer, the capabilities available for provisioning often appear to be unlimited and can be appropriated in any quantity at any time.
Measured service. Cloud systems automatically control and optimize resource use by leveraging a metering capability1 at some level of abstraction appropriate to the type of service (e.g., storage, processing, bandwidth, and active user accounts). Resource usage can be monitored, controlled, and reported, providing transparency for both the provider and consumer of the utilized service
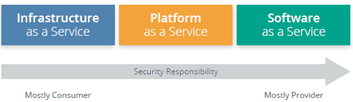
The Shared Responsibility Model:
Cloud Security & Compliance includes everything that security teams are currently responsible for today. All of the traditional domains remain, but the responsibility for implementing and managing controls are shared between the CSP and cloud service customer.
Responsibility for data security always remains the primary responsibility of the Data Owner/Cloud Service Customer (Your Organization).
However, controls, as they relate to physical hardware, privileged authorization, data segmentation, and adherence to compliance regulations will be shared between the cloud provider and cloud customer. Ownership of controls shared across the shared responsibilities model should be documented within contracts and service level agreements (SLAs). The Consuming organization should perform internal audits to measure the effectiveness and adherence to policy standards of the controls within their shared responsibility governance.
Third-party (external audits) should be leveraged when confirming the Cloud Service Providers side. These audits may take the form of:
- SOC-1 Type 2
- SOC-2 Type 2
- SOC-3
- FedRamp
- Iso27001
- PCI-DSS
- HIPAA/HITRUST
- FISMA Security Assessment
- Iso27017
- Iso27018
While some of these may not technically be audits (and take the form of certifications) - they are none-the-less valuable in assessing the control environment across different requirements.
Guidance, standards and requirements within this Primer have been established using the sources listed below:
The Federal Risk and Authorization Management Program (FedRAMP) is a government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services. FedRAMP enables Agencies to rapidly adapt from old, insecure legacy IT to mission-enabling, secure, and cost-effective cloud-based IT. FedRAMP created and manages a core set of processes to ensure effective, repeatable cloud security for the government. FedRAMP established a mature marketplace to increase utilization and familiarity with cloud services while facilitating collaboration across government through open exchanges of lessons learned, use cases, and tactical solutions. FedRamp: Governance: Link to Governance National Institute for Standards and Technology (NIST): Advises FedRAMP on FISMA compliance requirements and assists in developing the standards for the accreditation of independent 3PAOs FedRamp: Documents & Tools:· FedRAMP Annual Security Assessment Report (SAR) Template · FedRAMP Security Controls Baseline · Cloud Procurement Best Practices · FedRamp Security Assessment Framework Cloud Security Alliance: Link to CSAThe Cloud Security Alliance Cloud Controls Matrix (CCM) is specifically designed to provide fundamental security principles to guide cloud vendors and to assist prospective cloud customers in assessing the overall security risk of a cloud provider. The CSA CCM provides a controls framework that gives detailed understanding of security concepts and principles that are aligned to the Cloud Security Alliance guidance in 13 domains. The foundations of the Cloud Security Alliance Controls Matrix rest on its customized relationship to other industry-accepted security standards, regulations, and controls frameworks such as the ISO 27001/27002, ISACA COBIT, PCI, NIST, Jericho Forum and NERC CIP and will augment or provide internal control direction for service organization control reports attestations provided by cloud providers. Cloud Security Alliance’s Security Guidance for Critical Areas of Focus in Cloud ComputingThe Cloud Security Alliance (CSA), is dedicated to defining and raising awareness of best practices to help ensure a secure cloud computing environment, released the Guidance for Critical Areas of Focus in Cloud Computing 4.0. Guidance 4.0, which acts as a practical, actionable roadmap for individuals and organizations looking to safely and securely adopt the cloud paradigm, includes significant content updates to address leading-edge cloud security practices. CSA STAR RegistryThe Security Trust Assurance and Risk (STAR) Program encompasses key principles of transparency, rigorous auditing, and harmonization of standards. Companies who use STAR indicate best practices and validate the security posture of their cloud offerings. The STAR registry documents the security and privacy controls provided by popular cloud computing offerings. This publicly accessible registry allows cloud customers to assess their security providers in order to make the best procurement decisions. Center for Internet Security: CIS CloudNIST:
|
Contractual Areas of Concern:
- Make sure master service agreements (MSAs) captures all clauses, provisions, requirements (ex. How the data can be used/shared).
- Make sure Statements of Work contain detailed activities – KPIs – Roles & Responsibilities
- Service-Level Agreements contain service deliverables – have an ongoing reporting mechanism (monthly or quarterly metrics – reports that measure performance standards). Restitution
- Establish termination criteria – allows organization an out if CSP is performing poorly and putting the organization at risk.
- Restrictions on where Data can be stored Geographical restrictions – laws – client requirements – DR Implications.
- Business Associate Agreements - HIPAA
Risk Management:Performing risk-assessment is a necessary due-diligence task, and one that should be performed to gain an understanding for risk, threats, and other potential harms. You can leverage frameworks and guides by ENISA and CSA below when building a risk perspective about cloud use. ENISA (European Union Agency for Cybersecurity) Benefits, risk, and recommendation for Information security. CSA Series- Think OWASP but for Risk | Threats in the Cloud. o The Notorious 9 (2013) o Treacherous 12 (2016) o Egregious 11 (2019) Your organizations Enterprise Risk Management function. |
Cloud Related Definitions:
- Cloud Service Provider (CSP): A company that provides cloud-based platform, infrastructure, application, or storage services to other organizations or individuals, usually for a fee; otherwise known to clients “as a service.”
- Crypto Shredding – The process of encrypting data via multiple keys, and permanently destroying the keys so that encrypted data is no longer “recoverable”.
- Data Controller: The natural or legal person, public authority, agency, or any other body that alone or jointly with others determines the purposes and means of the processing of personal data. Where the purposes and means of processing are determined by national or community laws or regulations, the controller or the specific criteria for his nomination may be designated by national or community law.
- Data Dispersion: A technique in which data is sliced into chunks that are encrypted along with parity bits, and written to various drives in the cloud storage cluster
- Data Owner: The organization that has collected or created the data.
- Data Processor: Any entity acting on behalf or at the behest of the data controller, performing any manipulation, storage, or transmission of the PII. In the cloud motif, the data processor is the cloud service provider.
- Infrastructure as a Service (IaaS): The capability provided to the consumer is to provision processing, storage, networks, and other fundamental computing resources where the consumer is able to deploy and run arbitrary software, which can include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, and deployed applications; and possibly limited control of select networking components (e.g., host firewalls).: NIST SP 800-145
- Platform as a Service (PaaS): The capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created or acquired applications created using programming languages, libraries, services, and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, or storage, but has control over the deployed applications and possibly configuration settings for the application-hosting environment. NIST SP 800-145
- Private cloud: The cloud infrastructure is provisioned for exclusive use by a single organization comprising multiple consumers (e.g., business units). It may be owned, managed, and operated by the organization, a third party, or some combination of them, and it may exist on or off premises. NIST SP 800-145
- Public cloud: The cloud infrastructure is provisioned for open use by the general public. It may be owned, managed, and operated by a business, academic, or government organization, or some combination of them. It exists on the premises of the cloud provider. NIST SP 800-145
- Software as a Service (SaaS): Software as a Service (SaaS). The capability provided to the consumer is to use the provider’s applications running on a cloud infrastructure. The applications are accessible from various client devices through either a thin client interface, such as a web browser (e.g., web-based email), or a program interface. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage, or even individual application capabilities, with the possible exception of limited user specific application configuration settings. - NIST SP 800-145






Leave A Reply