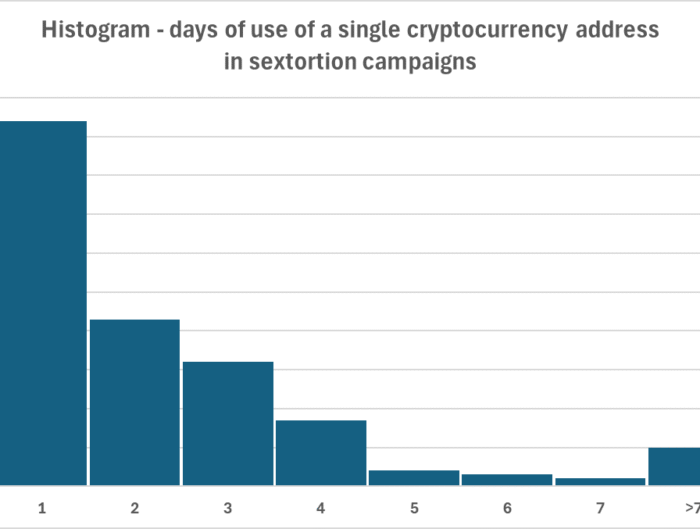
A quick look at sextortion at scale: 1,900 messages and 205 Bitcoin addresses spanning four years, (Tue, Sep 2nd) SANS Internet Storm Center, InfoCON: green
What can almost 2,000 sextortion messages tell us about how threat actors operate and whether they are successful? Let's find out. What can almost 2,000 sextortion messages tell us about how …