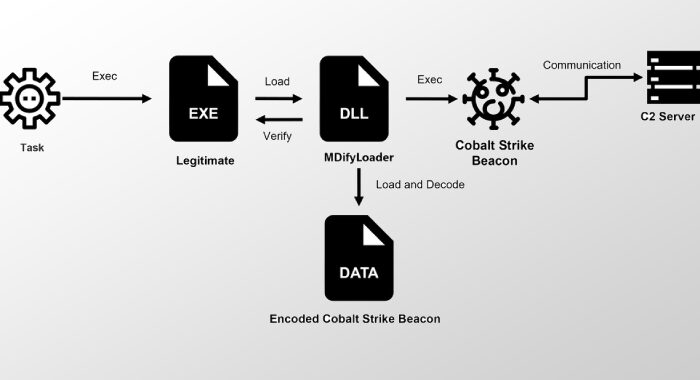
Hackers Exploit Critical CrushFTP Flaw to Gain Admin Access on Unpatched Servers The Hacker [email protected] (The Hacker News)
A newly disclosed critical security flaw in CrushFTP has come under active exploitation in the wild. Assigned the CVE identifier CVE-2025-54309, the vulnerability carries a CVSS score of 9.0. "CrushFTP 10 …