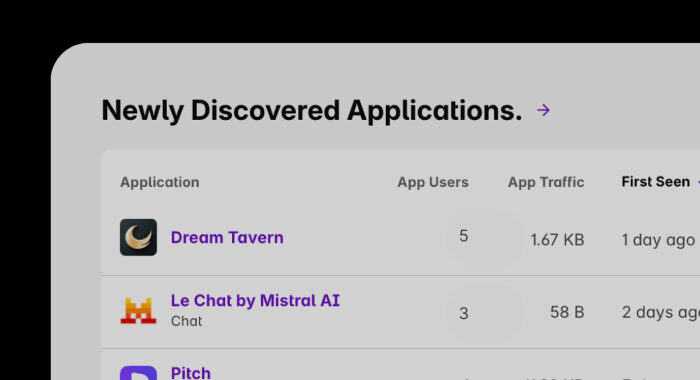
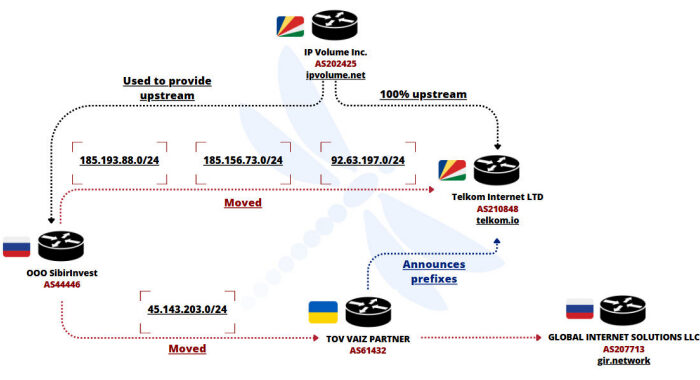
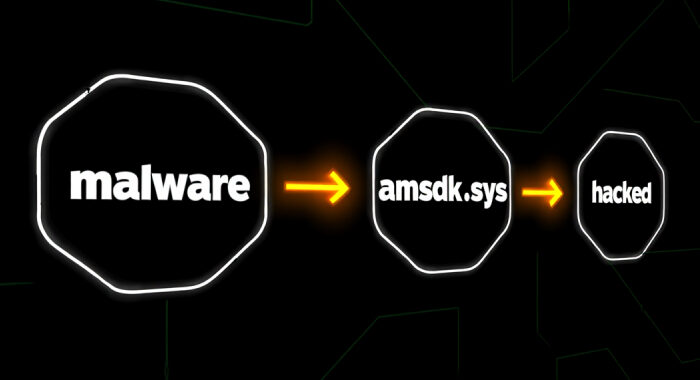
Lazarus Group Expands Malware Arsenal With PondRAT, ThemeForestRAT, and RemotePE The Hacker Newsinfo@thehackernews.com (The Hacker News)
The North Korea-linked threat actor known as the Lazarus Group has been attributed to a social engineering campaign that distributes three different pieces of cross-platform malware called PondRAT, ThemeForestRAT, and …