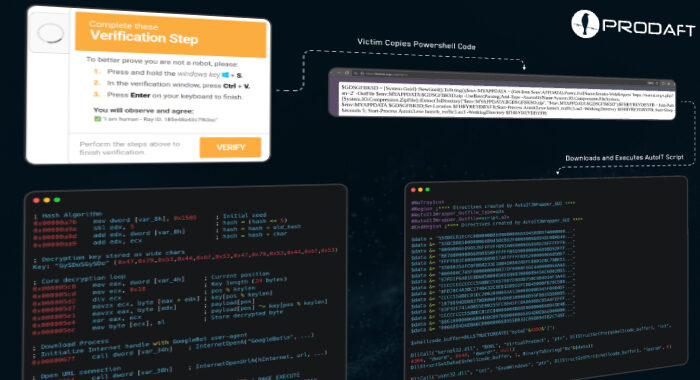
Fire Ant Exploits VMware Flaws to Compromise ESXi Hosts and vCenter Environments The Hacker [email protected] (The Hacker News)
Virtualization and networking infrastructure have been targeted by a threat actor codenamed Fire Ant as part of a prolonged cyber espionage campaign. The activity, observed this year, is primarily designed Now …