Why the Old Ways Are Still the Best for Most Cybercriminals darkreadingJon Clay
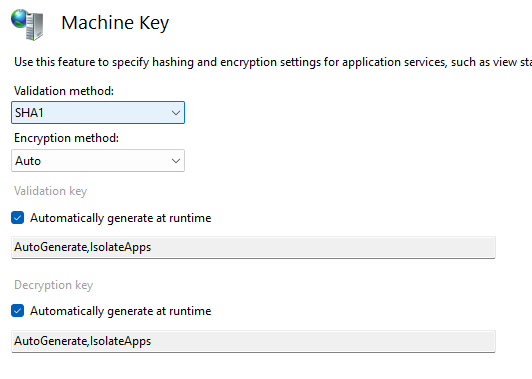
While the cybercrime underground has professionalized and become more organized in recent years, threat actors are, to a great extent, still using the same attack methods today as they were …