⚡ Weekly Recap: BadCam Attack, WinRAR 0-Day, EDR Killer, NVIDIA Flaws, Ransomware Attacks & More The Hacker [email protected] (The Hacker News)
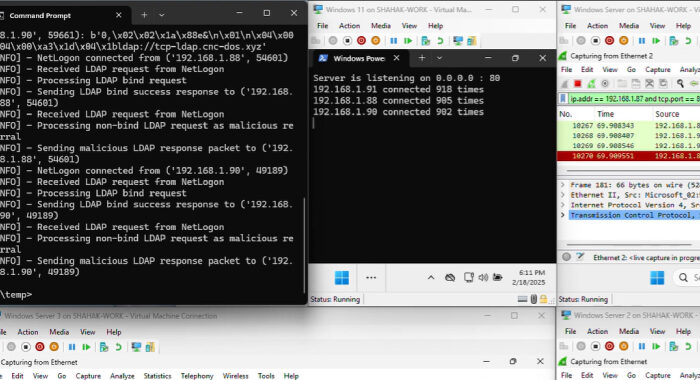
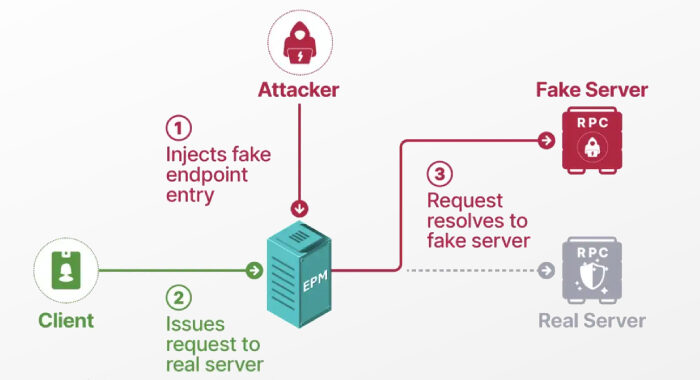
This week, cyber attackers are moving quickly, and businesses need to stay alert. They’re finding new weaknesses in popular software and coming up with clever ways to get around security. …