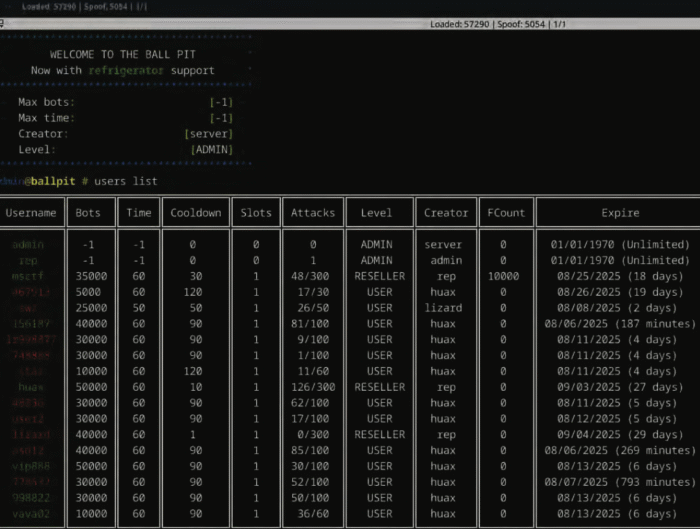
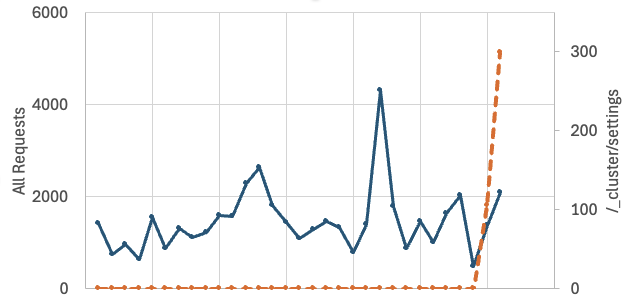
Russian Hacktivists Take Aim at Polish Power Plant, Again darkreadingKristina Beek
This attack was seemingly more successful than the first iteration, causing disruptions at the plant. This attack was seemingly more successful than the first iteration, causing disruptions at the plant. Read More