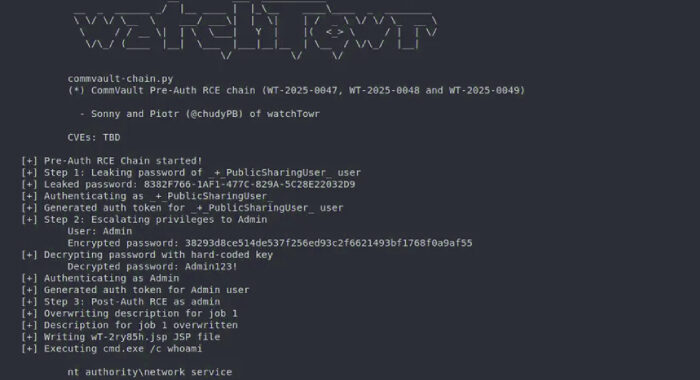
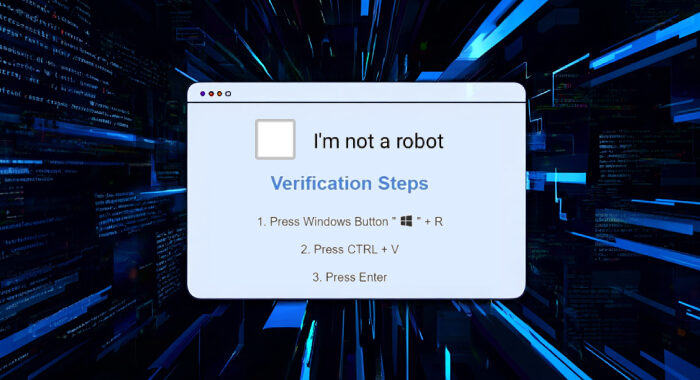
Hackers Abuse VPS Infrastructure for Stealth, Speed darkreadingAlexander Culafi
New research highlights how threat actors abuse legitimate virtual private server offerings in order to spin up infrastructure cheaply, quietly, and fast. New research highlights how threat actors abuse legitimate virtual …