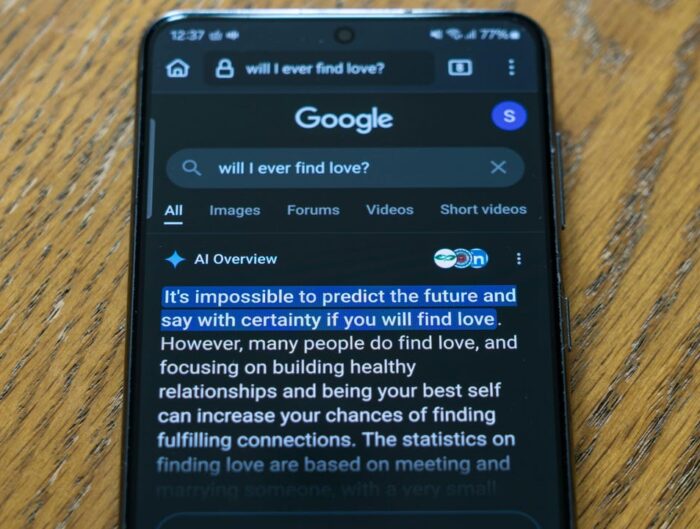
FTC Chair Tells Tech Giants to Hold the Line on Encryption darkreadingKristina Beek
The chairman sent letters out to companies like Apple, Meta, and Microsoft, advising them not to adhere to the demands of foreign governments to weaken their encryption. The chairman sent letters …