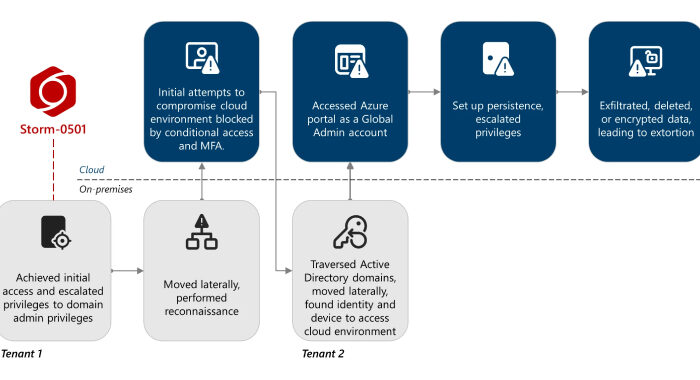
Google: Salesforce Attacks Stemmed From Third-Party App darkreadingElizabeth Montalbano, Contributing Writer
A group tracked as UNC6395 engaged in "widespread data theft" via compromised OAuth tokens from a third-party app called Salesloft Drift. A group tracked as UNC6395 engaged in "widespread data theft" …