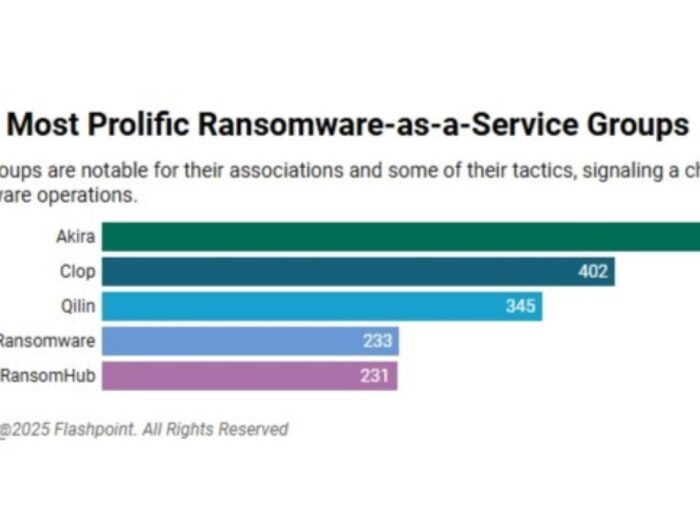
Akira, Clop Top List of 5 Most Active Ransomware-as-a-Service Groups darkreadingArielle Waldman
Flashpoint published its 2025 mid-year ransomware report that highlighted the top five most prolific groups currently in operation. Flashpoint published its 2025 mid-year ransomware report that highlighted the top five most …