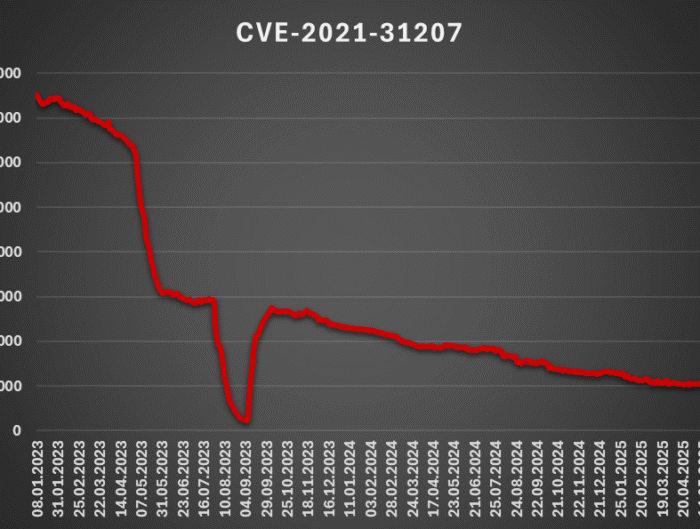
How quickly do we patch? A quick look from the global viewpoint, (Mon, Jul 21st) SANS Internet Storm Center, InfoCON: green
Since the ongoing âToolShellâ exploitation campaign, in which threat actors attack on-premise Sharpoint servers using a chain of two recently published vulnerabilities[1,2,3], is still on top of the cyber security …