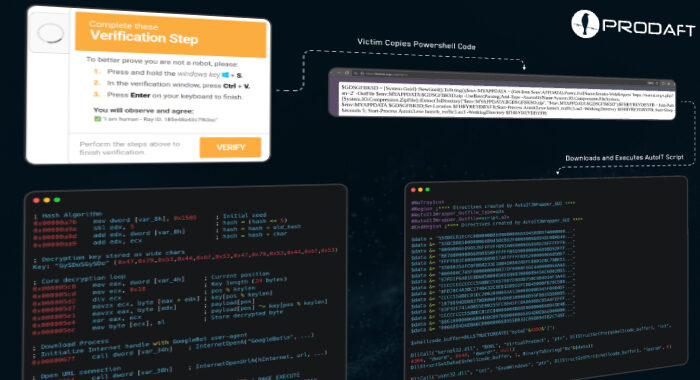
Critical Mitel Flaw Lets Hackers Bypass Login, Gain Full Access to MiVoice MX-ONE Systems The Hacker [email protected] (The Hacker News)
Mitel has released security updates to address a critical security flaw in MiVoice MX-ONE that could allow an attacker to bypass authentication protections. "An authentication bypass vulnerability has been identified in …