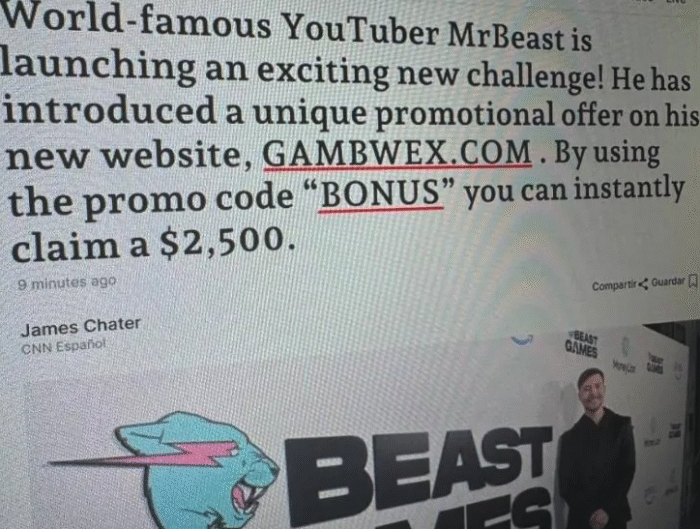
Tonic Security Harnesses AI to Combat Remediation Challenges darkreadingArielle Waldman
Attackers are becoming faster at exploiting vulnerabilities but this startup seeks to stop threats before they lead to breaches. Attackers are becoming faster at exploiting vulnerabilities but this startup seeks to …