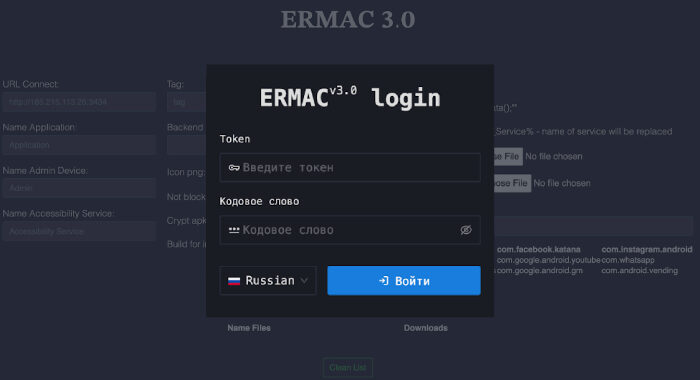
ERMAC V3.0 Banking Trojan Source Code Leak Exposes Full Malware Infrastructure The Hacker [email protected] (The Hacker News)
Cybersecurity researchers have detailed the inner workings of an Android banking trojan called ERMAC 3.0, uncovering serious shortcomings in the operators' infrastructure. "The newly uncovered version 3.0 reveals a significant evolution …