Anthropic AI Used to Automate Data Extortion Campaign darkreadingRob Wright
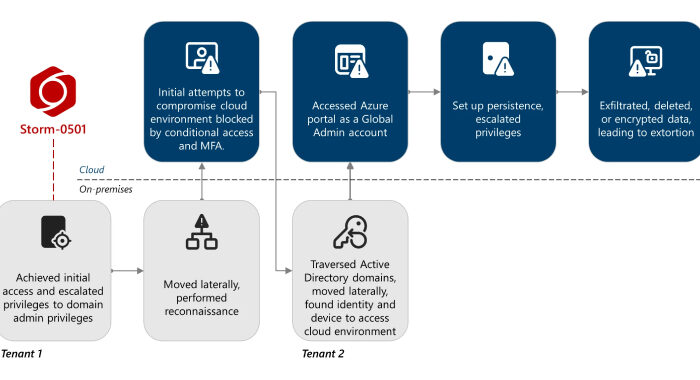
The company said the threat actor abused its Claude Code service to "an unprecedented degree," automating reconnaissance, intrusions, and credential harvesting. The company said the threat actor abused its Claude Code …