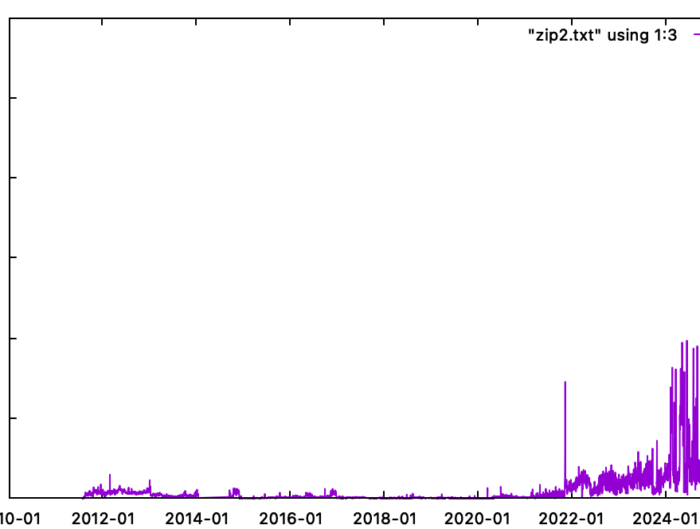
Increasing Searches for ZIP Files, (Thu, Aug 28th) SANS Internet Storm Center, InfoCON: green
I noticed recently that we have more and more requests for ZIP files in our web honeypot logs. Over the last year, we have had a substantial increase in these …