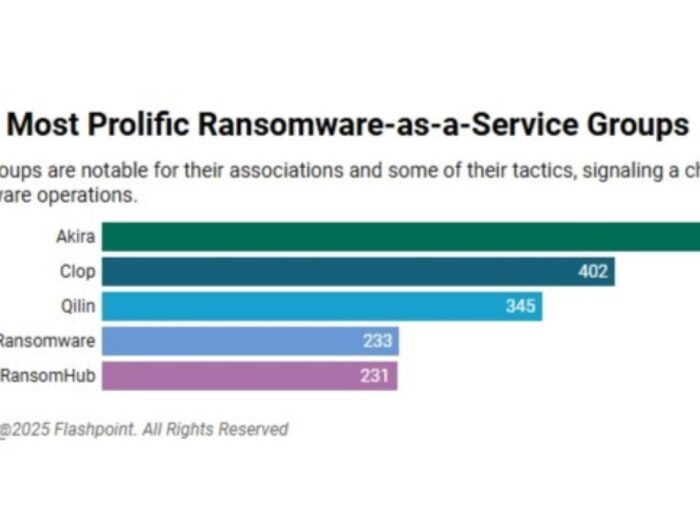
The credit reporting agency said the breach was "limited to specific data elements" and didn't include credit reports or core credit information. The credit reporting agency said the breach was "limited …
- Iran MOIS Phishes 50+ Embassies, Ministries, Int’l Orgs darkreadingNate Nelson, Contributing Writer
- Japan, South Korea Take Aim at North Korean IT Worker Scam darkreadingRobert Lemos, Contributing Writer
- Russia’s APT28 Targets Microsoft Outlook With ‘NotDoor’ Malware darkreadingRob Wright
- Cloudflare Holds Back the Tide on 11.5Tbps DDoS Attack darkreadingKristina Beek
- Malicious npm Packages Exploit Ethereum Smart Contracts to Target Crypto Developers The Hacker [email protected] (The Hacker News)
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)by Tech Jacks
- Tips and Tricks to Enhance Your Incident Response Proceduresby Tech Jacks
- Building a Security Roadmap for Your Company: Strategic Precision for Modern Enterprises by Tech Jacks
- The Power of Policy: How Creating Strong Standard Operating Procedures Expedites Security Initiativesby Tech Jacks
- Building a Future-Proof SOC: Strategies for CISOs and Infosec Leaders by Tech Jacks
- Security Gate Keeping – Annoying – Unhelpfulby Tech Jacks
- The Beginner’s Guide to Using AI: 5 Easy Ways to Get Started (Without Accidentally Summoning Skynet)